You have a right to exist, only if we give it to you
Investigating the wins and losses of empire at this stage of the game.
The exceptional and indispensable people are still working on their strong and unreasonable hope closely allied to a hot case of Clinical Psychopathy* that they are still exceptional and indispensable and must be obeyed. Productive activity in the Western Climes must be suffering greatly, because all of the bureaucrats with massive support structures are out in the wild, trying very hard to find their relevance again. They follow Mr Lavrov if he visits African countries and attempt to undo any positive work done. They are supposedly back in the South Pacific, attempting to create new relationships.
But what they stubbornly will not do, is let go of their now cratering unipolarity.
Here is Madame Yellen, feverishly written in an article from Foreign Policy. In reality, the article sounds quite sober but oh man, the clanger! This is what Yellen’s speech looks like through Foreign Policy eyes:
“The United States remains the most dynamic and prosperous economy in the world.” So, Yellen insists, America has no reason to seek to “stifle China’s economic and technological modernization” or to pursue a deep decoupling. America’s economic power, the Treasury secretary goes on, “is amplified” by its relationships with “close friends and partners in every region of the world, including the Indo-Pacific.” America thus has “no reason to fear healthy economic competition with any country.” And then Yellen delivers the punchline:
“China’s economic growth need not be incompatible with U.S. economic leadership.”
They will not give up and become a normal country because they suffer from Psychopathy which they define at a planetary level and in perpetuity.
The Financial Times reports that “talk of war between the US and China has become “commonplace” in Washington. “Many influential people seem to think that a US-China war is not only possible but probable”. “US officials are now looking at the cold war — not as a warning, but as a potential model”. While it’s already waging a proxy war against Russia (a nuclear power), the US wants to wage another war on China (a nuclear power). https://archive.is/2023.04.24-220757/https://www.ft.com/content/44fb5a00-e7b8-48bf-be20-5f72b2d4a048
It is so that many observers see the real pivot to China take a visible shape, which is not a friendly one. US Congress introduced 273 bills or amendments containing the word “China” in the first three months of the 118th Congress. A Financial Times article talks about the ‘points that the current administration has put on the board’ and they think they are doing well. But, China does not speak to them hence they live in a bubble.
Yellen says:
“China must accept America’s demarcation of the status quo. If it doesn’t respect the boundaries drawn for it by Washington between harmless prosperity and historically consequential tech development, then it should expect to face massive sanctions.” https://t.co/8rSrSR3mEC
Nicholas Burns, American ambassador to Beijing, says:
The US ambassador in Beijing called China a more serious challenge for the country than the USSR at the time. He also noted that the United States would like to avoid an accidental conflict with China. He noted that China is now a more serious challenge for the United States than the Soviet Union once was.
Congress follows:
US Senate should begin work on new legislation to strengthen export control laws and define new sanctions to counter China.
There are copious numbers of examples of the US plus its cronies still in the mindset that they are the leaders and will be the leaders in perpetuity. This power balance is what is changing and the US cannot abide it. They will fight, even when the fight seems hopeless.
They have had some wins and we should recognize these.
Counting Empire Wins:
It should be noticed that we are in a sense ‘living in the leap’ and these wins and the following empire defeats are sketches of the current situation. Things can and will change and it may get worse.
Europe, which now are complete vassals, including countries that held out initially, is an empire win.
The Philippines now has four more US bases but there is a great lash back. The Philippines is probably today the richest study of how not to take sides and what happens if you do. https://www.globaltimes.cn/page/202305/1290194.shtml
South Korea, whose leader even sang for Biden like a good vassal would do.
Australia is being turned into a US military base with Kangaroos.
In the South Pacific the US’ is scrambling for whatever they can get: A new embassy in Tonga this month and continual engagement with Islands states such as Vanuatu and Kiribati about opening proposed new embassies in those countries. Joe Biden will make a historic visit to Papua New Guinea (PNG) on May 22, becoming the first sitting US president to visit the country in at least a century. There also a new embassy in Solomon Islands yet their leaders understand that China holds their economic future in the region.
Every step of US’ promotion of ties with South Pacific countries seems to be saying ”America is back.” But what’s really back is the US’ utilitarianism, as well as the weaponization of regional countries.
NATO will open a liaison office in Tokyo, the first of its kind in Asia, to allow the military alliance to conduct periodic consultations with Japan and key partners in the region, such as South Korea, Australia and New Zealand.
China is not speaking to the US. Trying to force communication, Taiwan was promised another cache of weapons.
With this flurry of activity, who is at home minding the US store? Is it surprising that economic activity is dropping like a stone? They are trying to win the world, but they are losing themselves.
Nobody is under any illusions though. After all, what Pacific island countries would anticipate from the US is further exploitation of their strategic resources, without any genuine respect. The rhetoric that the US is going to be back to the South Pacific would be interpreted as an ominous signal for the island nations to be instrumentalized or even weaponized.
The technology employed by the hegemon is same old same old, we have seen it a number of times and it does not change.
It is from this point onwards that we can count empire defeats. They are however more subtle and I would say, the fangs are sharper and cut deeper as we are seeing events ‘not seen in a hundred years’.
Counting Empire Defeats
Donald Ramotar, former president of Guyana: “Despite the propaganda offensive against China, China’s reputation as a reliable partner and a real friend to developing countries continues to grow. And as China’s reputation grows, US hostility increases, bringing exploitation.” Africa as a whole is still teetering between ties with the hegemon and with multipolarity. It is a country-by-country measure, and it is difficult to cut ties completely. The tendency overall is more towards China than to Russia which is not strange.
China in the meantime, gave exactly the right information at exactly the right time. They published a technical document explaining how the US does color revolutions but this time, they called the name – CIA. I copy the full document here:
The CIA’s Five Color Revolution Methods – Wu Zhichao, Ed.
China cyber attacks linked to the CIA
The Central Intelligence Agency (CIA), a more well-known name than the National Security Agency (NSA), is one of the main intelligence agencies of the US federal government. It is headquartered in Langley, Virginia, USA. The Intelligence Division (DI), the Covert Operations Division (NCS), the Technology Division (DS&T), and the Support Division (DS) are four departments. Its main business scope involves: collecting intelligence information of foreign governments, companies and citizens; comprehensively analyzing and processing intelligence information collected by other US intelligence agencies; providing national security intelligence and security risk assessment opinions to high-level US decision makers; organizing implementation and Guiding and supervising cross-border secret activities, etc.
For a long time, the US Central Intelligence Agency (CIA) has secretly implemented “peaceful evolution” and “color revolutions” around the world, and has continued to carry out espionage and stealing activities.
Since entering the 21st century, the rapid development of the Internet has provided new opportunities for the US Central Intelligence Agency (CIA) to infiltrate, subvert and sabotage activities. Organizations and individuals using US Internet equipment and software products around the world have become (CIA)’s puppet “agents”, helping the agency quickly become a dazzling “star” in the cyber espionage war.
This series of reports starts with a large number of real cases that 360 and the National Computer Virus Emergency Response Center participated in the investigation, reveals the main details of their network attack weapons, and discloses the specific process of some typical network security cases that occurred in China and other countries. It is comprehensive and in-depth. This paper analyzes the US Central Intelligence Agency (CIA)’s cyber attack stealing and related real-life harm activities, as well as its contribution to the United States becoming a “Matrix”, and provides reference and suggestions for victims of cyber attacks all over the world.
Overview
From the impact of the international socialist camp in the 1980s, the upheaval in the Soviet Union and the East (“Velvet Revolution”) in the early 1990s to the “Rose Revolution” in Georgia in 2003, from the “Orange Revolution” in Ukraine in 2004 to the “Tulip Revolution” in Kyrgyzstan in 2005, From the “Arab Spring” in West Asian and North African countries in 2011 to the “Second Color Revolution” in Ukraine in 2014 and the “Sunflower Revolution” in Taiwan, China, they were all recognized by international organizations and scholars around the world as “color revolutions” dominated by US intelligence agencies. Revolution” typical case. There have also been attempted “color revolutions” in some other countries, such as the “Snowflake Revolution” in Belarus in March 2005, the “Orange Storm” in Azerbaijan in June 2005, the “Cedar Revolution” in Lebanon in 2005, and the “Saffron Revolution” in Myanmar in 2007. “, Iran’s “Green Revolution” in 2009, and so on. If we count from the Cold War period, there are countless regime change events with the color of “peaceful evolution” and “color revolution”. According to statistics, over the past few decades, the US Central Intelligence Agency (CIA) has overthrown or attempted to overthrow at least 50 legitimate governments of other countries (while the CIA has only admitted 7 of them), causing turmoil in related countries.
Comprehensive analysis of various technologies in the above-mentioned incidents shows that information communication and on-site command become the decisive factors affecting the success or failure of the incident. These technologies of the United States are in a leading position in the world. Especially in the 1980s, the United States promoted the Internet to the world and was generally accepted by countries all over the world.
Former U.S. Secretary of State Albright once threatened: “With the Internet, we have a way to deal with China.”
This statement is true, many “color revolution” incidents have the shadow of Western powers fueling the flames with the help of the Internet. After the “Arab Spring” incidents in many countries in West Asia and North Africa, some large American multinational Internet companies actively intervened, invested a lot of manpower, material resources, and financial resources to all parties to the conflict, wooed and supported the opposition, and publicly challenged the legitimate governments of other countries that did not match the interests of the United States. Assist in the dissemination of false information, and promote the intensification of public protests.
One is to provide encrypted network communication services. In order to help protesters in some countries in the Middle East keep in touch and avoid being tracked and arrested, an American company (reportedly with a background in the US military) has developed a TOR technology that can access the Internet and is untraceable (“Onion head” routing technology, The Onion Router). The servers in question encrypt all information that flows through them, helping certain users to surf the web anonymously. After the project was launched by American companies, it was immediately provided free of charge to anti-government personnel in Iran, Tunisia, Egypt and other countries to ensure that those “dissident youth who want to shake their own government’s rule” can avoid the scrutiny and monitor.
The second is to provide offline communication services. In order to ensure that anti-government personnel in Tunisia, Egypt and other countries can still keep in touch with the outside world, Google and Twitter quickly launched a special service called “Speak2Tweet”, which allows users to dial and upload voice for free Leave a message, these messages are automatically converted into tweets and then uploaded to the Internet, Twitter and other platforms for public release, completing the real-time report on the scene of the incident.
The third is to provide on-site command tools for rallies and parades based on the Internet and wireless communications. The RAND Corporation of the United States has spent several years developing a non-traditional regime change technology called “swarming”, which is used to help a large number of young people connected through the Internet join the mobile protests of “one shot for another place”, greatly Improve the efficiency of on-site command of the event.
Fourth, an American company has developed a software called “Riot”, which supports 100% independent wireless broadband network, provides variable Wi-Fi network, does not rely on any traditional physical access methods, and does not require telephone, cable or satellite connections. Can easily evade any form of government surveillance. With the help of the above-mentioned powerful network technology and communication technology means, the US Central Intelligence Agency (CIA) planned and organized a large number of “color revolution” events around the world.
Fifth, the U.S. State Department regards the research and development of the “anti-censorship” information system as an important task, and has injected more than 30 million US dollars into the project.
The CIA’s cyber attack weapons
On March 7, 2017, the WikiLeaks website disclosed 8,716 secret documents allegedly from the US Central Intelligence Agency (CIA) Network Intelligence Center, which involved the attack methods and attack operations of the US Central Intelligence Agency (CIA) hacker team. Code names, technical specifications and requirements of attack tools, etc., WikiLeaks called the relevant documents “Vault7” (dome 7), which has aroused great attention worldwide.
In 2020, Qihoo 360 independently discovered an APT organization that has never been exposed to the outside world. It specifically targets China and its friendly countries to carry out cyber attack and stealing activities. The victims are all over the world. We separately number it as APT-C-39. There is evidence that the organization uses cyber weapon tools (including Athena, Fluxwire, Grasshopper, AfterMidnight, HIVE, ChimayRed, etc.) associated with the exposed “Vault7” (dome 7) data to carry out cyber attacks against victims in China and other countries. The earliest attack activities can be traced back to 2011, and related attacks have continued to this day. The attacked targets involve various countries’ important information infrastructure, aerospace, scientific research institutions, petroleum and petrochemical, large Internet companies, and government agencies.
In large-scale global cyber attacks, the US Central Intelligence Agency (CIA) used a large number of “zero-day” (0day) vulnerabilities, including a large number of backdoors and vulnerabilities that have not been publicly disclosed so far (some functions have been verified), Establish “zombie” networks and attack springboard networks around the world, and attack and invade in stages against network servers, network terminals, switches and routers, as well as a large number of industrial control equipment. We have successfully extracted several “Vault7” (dome 7) network attack weapon samples in the cyber attack operations that have been discovered specifically targeting targets in China, and several Southeast Asian countries and European partners have also extracted almost identical The samples mainly include:
Fluxwire (flux wire) backdoor program platform
A complex backdoor attack operation management platform that supports 9 mainstream operating systems such as Windows, Unix, Linux, and MacOS and 6 different network architectures. It can form a mesh network with many “broiler” nodes that can operate completely autonomously, supporting self-repair, Loop attack and multipath routing.
Athena (Athena) program
A lightweight backdoor program for the Microsoft Windows operating system, jointly developed by the US Central Intelligence Agency (CIA) and the US company Siege Technologies (acquired by Nehemiah Security in 2016), which can be used for remote installation, supply chain attacks, and man-in-the-middle hijacking attacks It can be implanted by means of physical contact installation, etc., and resides in the form of Microsoft Windows service. All attack function modules are decrypted and executed in memory in the form of plug-ins. 2.3 Grasshopper (grasshopper) backdoor program An advanced configurable backdoor program for the Microsoft Windows operating system, which can generate malicious loads in various file formats (EXE, DLL, SYS, PIC), supports multiple execution modes, and can be concealed after being equipped with different plug-in modules. Stay and perform spy functions.
AfterMidnight (after midnight) backdoor program
A lightweight backdoor that runs as a DLL service in the Microsoft Windows operating system. It dynamically transmits and loads the “Gremlins” module through the HTTPS protocol, and executes the malicious load in an encrypted manner throughout the process.
ChimayRed (Chimay Red Hat) Vulnerability Exploitation Tool
A vulnerability exploit kit for MikroTik and other brands of routers, which can be used to implant lightweight network device backdoor programs such as “TinyShell” with exploits. 2.6 HIVE (Honeycomb) Network Attack Platform The “Hive” network attack platform was jointly developed by a department of the US Central Intelligence Agency (CIA) and a company owned by the famous US military enterprise Northrop Grumman (NOC). It provides the network attack team of the US Central Intelligence Agency (CIA) A persistent attack stealing method with complex structure. It manages and utilizes a large number of lost assets around the world, forms multi-layer dynamic springboards and secret data transmission channels, and uploads user accounts, passwords and private data to the US Central Intelligence Agency (CIA) 7×24 hours (https://www. cverc.org.cn/head/zhaiyao/news20220419-hive.htm).
Other Derivatives In the process of attacking and stealing secrets through the above-mentioned “Vault7” (Dome 7) cyber weapon, the US Central Intelligence Agency (CIA) also derived and used a large number of attack samples other than “Vault7” (Dome 7) data, and the samples that have been extracted These include disguised phishing software installation packages, keylogger components, system information collection components, USB file stealing modules, and different open source hacking tools.
Functional Analysis of the Cyber Attack Weapon Samples of the US Central Intelligence Agency (CIA)
During the investigation of many typical cyber attacks in China, Qihoo 360 captured and successfully extracted a large number of data closely related to the Internet exposure of the US Central Intelligence Agency (CIA) “Vault 7” from the information network of the victim unit. Trojan horse programs, function plug-ins and attack platform samples. In-depth analysis found that most of the relevant program samples follow the Network Operations Division In-memory Code Execution Specification, Network Operations Division Cryptographic Requirements, and Network Operations Division Persisted DLL Specification in the “Vault7” (dome 7) data, etc. of the US Central Intelligence Agency (CIA) Malware development standards and technical specifications. These standards and norms respectively correspond to the loading and execution of malicious code, data encryption and persistence behaviors in cyber attack stealing activities, and relevant cyber weapons have undergone extremely strict standardized, process-oriented and professional software engineering management. It is reported that currently only the US Central Intelligence Agency (CIA) strictly abides by these standards and specifications to develop cyber attack weapons.
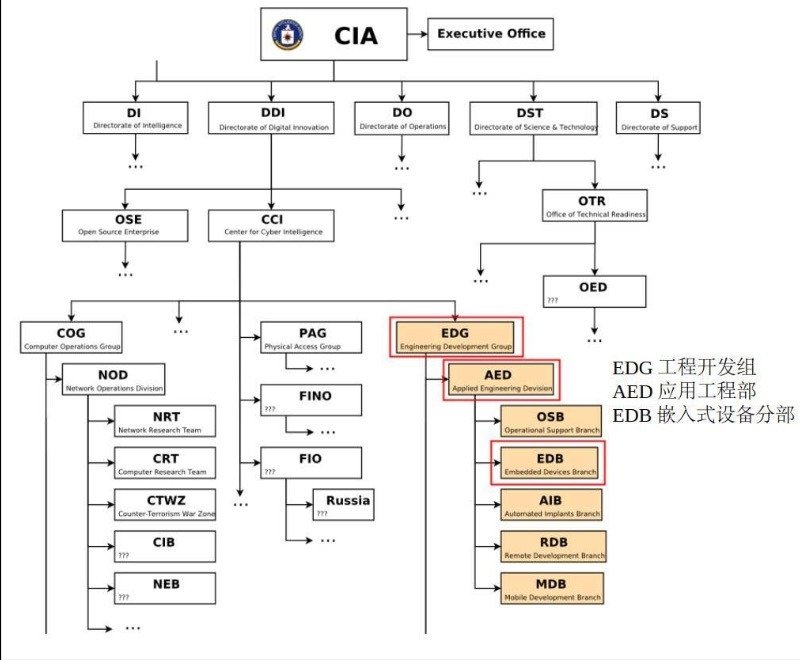
According to “Vault7” (dome 7) data, the above-mentioned cyber attack weapons belong to the EDG (Engineering Development Group) of the US Central Intelligence Agency (CIA), and its subordinate AED (Application Engineering Department) and EDB (Embedded Device Division) ) and other independent or joint research and development divisions. Most of these cyber weapons were born in a top secret internal network of the US Central Intelligence Agency (CIA) called “devlan.net“.”devlan.net” is a huge network weapons development and testing infrastructure established by the Engineering Development Division (EDG) of the US Central Intelligence Agency (CIA). According to the development log data of “devlan.net“, at least 200 engineers from EDG have been invested in the research and development of the “HIVE” (honeycomb) project alone.
Further technical analysis found that most of the backdoor programs and attack components of the US Central Intelligence Agency (CIA) run in the form of memory-resident execution without physical files, which makes it extremely difficult to discover and obtain evidence for relevant samples. Even so, the joint technical team managed to find an effective solution to the forensics challenge. For the convenience of subsequent description and analysis, we temporarily divide the attack weapons of the US Central Intelligence Agency (CIA) into 9 categories:
Framework platform classes. We discovered and captured attack samples and activities of Fluxwire (magnetic flux lines), Grasshopper (grasshopper), and Athena (Athena). Dome 7) The descriptions in the materials are confirmed one by one.
Attack module delivery class. The U.S. Central Intelligence Agency (CIA) has used a large number of small malicious code downloaders with simple functions to load and execute more malicious codes and modules. The relevant samples have no special malicious functions and characteristics, but they cooperate with attack weapons such as framework platforms However, it can show a powerful secret-stealing function, and it is extremely difficult to attribute it to the source.
Remote control class. A variety of remote control plug-ins have been extracted, most of which are attack module components derived from framework platform attack weapons, and the two cooperate with each other.
Lateral Movement Classes. Among the large number of malicious program samples extracted, there are many backdoor programs installed and implanted by using Windows remote services with system administrator credentials. In addition, the U.S. Central Intelligence Agency (CIA) also hijacked the upgrade programs of various security products on the intranet, issued and installed backdoor programs through the upgrade function of the intranet upgrade server, and carried out lateral movement attacks on the intranet.
Information collection and theft. The joint technical team accidentally extracted an information-stealing tool used by the US Central Intelligence Agency (CIA). NSA) dedicated information-stealing tool. This situation shows that the US Central Intelligence Agency (CIA) and the US National Security Agency (NSA) will jointly attack the same victim, or share cyber attack weapons with each other, or provide relevant technical or human support. This adds important new evidence to the attribution of the identity of the APT-C-39 attackers.
Vulnerability Exploitation Class. The investigation found that since at least 2015, the US Central Intelligence Agency (CIA) has established a huge springboard resource for cyber attacks around the world, using “zero-day” (0-day) vulnerabilities to attack global IOT (Internet of Things) devices and Attack network servers indiscriminately, and convert a large number of lost devices into springboard “broilers”, or hide their own attack behavior, or blame network attacks on other countries.For example, the US Central Intelligence Agency (CIA) used a vulnerability attack kit code-named “ChimayRed” (Chimay Red Hat) to target multiple models of MikroTik brand routers, including a large number of network devices using such routers in China. During the attack, the US Central Intelligence Agency (CIA) will first maliciously modify the router startup script, so that the router will still execute the backdoor program after restarting; then, the US Central Intelligence Agency (CIA) will modify the router’s CGI program to block the (CIA) to prevent other attackers from re-invading and causing loss of authority; eventually, the US Central Intelligence Agency (CIA) will implant “Hive” (HIVE) or “TinyShell” into the router, which only the US Central Intelligence Agency (CIA) ) exclusive backdoor program that can be used.
Masquerading as normal software. According to the network environment of the attack target, the US Central Intelligence Agency (CIA) customized and disguised the backdoor program as an unpopular software installation package used by the target with a small number of users, and carried out precise social engineering attacks on the target.
Attack and defense of security software. The US Central Intelligence Agency (CIA) has mastered attack tools specially used to attack commercial anti-virus software. Through these special tools, the process of designated anti-virus software can be shut down and killed remotely, so that the relevant anti-virus software can attack the US Central Intelligence Agency (CIA). Behavioral or offensive weapons are ineffective.
Third-party open source tools. The US Central Intelligence Agency (CIA) also often uses off-the-shelf open source hacking tools to carry out attacks. The initial attacks of the CIA’s cyber attack operations generally target the victim’s network equipment or servers, as well as social engineering attacks. After obtaining the target authority, it will further explore the network topology of the target organization, and move laterally to other networked devices in the internal network to steal more sensitive information and data. The target computer controlled by the US Central Intelligence Agency (CIA) will be monitored in real time for 24 hours. All keyboard strokes of the victim will be recorded, and information copied and pasted from the clipboard will be stolen. USB devices (mainly mobile hard drives) , U disk, etc.) will also be monitored in real time. Once a USB device is connected, the private files in the victim’s USB device will be automatically stolen. When conditions permit, the camera, microphone and GPS positioning device on the user terminal will be remotely controlled and accessed.
Summary
The cyber hegemony manipulated by the United States originated in cyberspace, covers the world, and affects the whole world. As one of the three major intelligence-gathering agencies in the United States, the Central Intelligence Agency (CIA) has already shown automation, systematization and intelligence in its cyber attacks against the world. characteristics. The 8,716 documents leaked from the WikiLeaks website alone contain many important hacking tools and cyber attack weapons of the U.S. intelligence agencies, indicating that the U.S. has built the world’s largest cyber arsenal. Through empirical analysis, we found that its cyber weapons use extremely strict espionage technical specifications, and various attack methods echo and interlock. It has now covered almost all Internet and IoT assets in the world, and can control other countries’ networks anytime, anywhere. Stealing important and sensitive data from other countries will undoubtedly require a lot of financial, technical and human resources to support it. The US-style cyber hegemony is evident, and the “Matrix” is well-deserved.
This series of reports attempts to disclose the long-term attacks and stealing activities of the US Central Intelligence Agency (CIA) targeting network targets in China, and initially explores these network attacks and data theft activities.
In response to the highly systematic, intelligent, and concealed cyber attacks launched by the US Central Intelligence Agency (CIA) against my country, how can domestic government agencies, scientific research institutions, industrial enterprises, and commercial organizations quickly “see” and “handle” them immediately? “Particularly important. In order to effectively deal with imminent network and real threats, while adopting self-controllable localized equipment, we should organize and carry out self-inspection and self-inspection of APT attacks as soon as possible, and gradually establish a long-term defense system to achieve comprehensive and systematic prevention and control , against advanced threat attacks. The Paper
The Pentagon requested a meeting between US Defence Secretary Lloyd Austin and Chinese Defence Minister Li Shangfu in Singapore in June, despite China’s earlier refusal. A meeting would be awkward since the US slapped sanctions on Mr. Li in 2018 for buying Russian defense equipment. China is talking to a lot of people, but not to the US. The US was warned during the Nancy Pelosi Taiwan visit that China will close down certain communication channels, and now they have done so.
I cannot stress enough how big a win this is. China opens an office in Okinawa, which is now called Ryukyu. This is not a small island state in the middle of the Pacific but is the center of the warfighting domain of the US in the Pacific region. Beijing recognizes Ryukyu. China will officially call Okinawa prefecture by its original, pre-Japanese name “琉球”, Ryukyu. Wu Jianghao, China’s ambassador to Japan, met with Yoshimi Teruya, Deputy Governor of Okinawa, in Tokyo for a long closed-door meeting, before making the announcement. China will open a regional diplomatic office in Ryukyu and the current Governor of Okinawa Prefecture, Denny Tamaki, will visit China this month. FM Qing Gang, on April 21st at Lanting Forum, referenced both the Cairo Declaration and the Potsdam Proclamation in relation to Taiwan, both of which state that “Ryukyu” isn’t part of Japan.
China’s Ambassador to the United States, after a three-hour private meeting with Hawaii’s Governor Waiheʻe, announced that China will refer to Hawaii as ‘The Kingdom of Hawaii’ from this date. The spokeswoman for NGO Independence Hawaii, Janeta Liliʻuoukalani, hailed the move, “All Hawaiians thank President Xi for our liberation and invite him to our Independence Day”.
Then the Chinese envoy to the EU spoke about the post-USSR space and literally said that those countries ‘do not have their driver’s licenses to drive a country’. Those are my words and certainly not a quote and in reality, he said that they are not fully established in International Law as the UN requires. This caused an outcry, but, he is right.
With these three examples, what is China doing? Going around all the US-established domains and sharply questioning their Western leadership and the basis on which they are established seems to me a huge win. Empire forces thrive on creating chaos by utilizing old wounds, left over from previous wars by design, or previous movement of country boundaries and establishment of new borders, as it pleases them. Division is their hope for Russia, as in their view, Russia is too big for them to conquer and of course, China must be divided.
Mr Putin dropped some reality: Russia won’t play by ‘rules’ imposed by the West and Russia will not abide by the invented “rules” someone seeks to impose on it, Vladimir Putin has said
From the LAC, the expression is that they want their continent to liberate itself from US/NATO occupation. From a redhot recent speech by rising star Camila Escalante, she asked:
When are we allowed to start asking what steps are being taken towards this, by the governments of Argentina, Brazil, Chile, Colombia, Honduras and Mexico?
If any one of these governments dared to stand up against the empire and expel the yanquis de mierda, they’d find themselves up against the gross all-out siege raining down on Nicaragua currently.
That is to reiterate, that the governments of Honduras and Mexico are under some level of siege for daring to take steps to implement more sovereign models. All of these governments were elected democratically, by the people and must be defended.
And then we see the aid that is cringe-worthy. Venezuelan people are suffering the most. The EU continues to provide humanitarian aid. Since 2018 we have contributed €540 million to address the migration crisis and urgent needs of millions of Venezuelans. It is essential that social & humanitarian agreement is implemented. So cynical. If the neocolonialists in the EU truly cared about Venezuelans, they would lift their illegal, murderous sanctions and give back the billions they stole from Venezuela’s central bank. Venezuela doesn’t need “humanitarian aid”; it wants the imperialist war on it to end
Today I will call the LAC a win, but it is thin. It is only by continual vigilance and pushback that they can keep their very small edge.
And then we see this: Organized by US SOUTHERN COMMAND, Chiles and US Special Forces execute operations in a combined environment. Organizado por el Comando Sur, las FFEE chilenas y de los EEUU ejecutan operaciones combinadas
Of course, most of the middle east is a win. I stress, for now!
Russia will win and China is sending their special military operatives to a special school in Russia for training. China will win.
The major win is, although we are in the middle of a war luckily not yet kinetic, that The West’s crusaders can no longer loot the world without blowback. And as so often been stated that if the Empire loses, it will go for the nukes.
—o0o—
Clinical Psychopathy* is used in a descriptive manner and certainly not in a psychologically accepted and correct manner.

Well done dear A. It’s a mixed bag. Empire continues to leverage the advantages, momentum and soft cultural power of generations. Like South African oligarchs, it continues to live off the considerable fat of the past.. It has brain washed billions through Hollywood, music industry, controlled education curricula in most… Read more »
Thank-you for the kind comments. I certainly have not written enough in the last month or so, but it has been a scramble to stay in touch with the major daily events. So, more will be incoming given that our world allows me the time to write. This morning seems… Read more »
Amarynth, when you have time your further thoughts on AI would be appreciated.
Really – we’re building one. I am not fully involved but part of giving feedback. I will say something when the time is right. At the moment things are firing on cylinders that we did not know they had lol!
Bravo Amarynth on this epic account of the tidal wave of concurrent events that is about to swamp NATOstan. And yes absolutely, the real wild card that remains is whether or not the West invokes the Sampson option. I love the powerplay that China is deploying regarding Okinawa and their… Read more »
powerful archive. thank you, amarynth, as steve & archeon have said, this is impressive! brilliant job.
Emersonreturn, “powerful archive”, yes, good description. When those Western leaders are wearing orange jumpsuits, tried for their crimes, it is this kind of detailed research they will be confronted with. I read it then looked for the NGO/university/government agency who put it together. This is not the work of days… Read more »
Boy o boy, what a great summary ! There was some work went into that !
“The West’s crusaders can no longer loot the world without blowback.”
Yes, the manifestation of this change is subtle, barely noticeable, but the Empire knows that a miscalculation could be fatal.
Amarynth, that was impressive, I am impressed. The thing is, if you stand back far enough it looks like the USA and her vassals are the ones under attack. If Putin and XI were directly calling the shots to undermine the Empire from within, they could hardly do more damage… Read more »
“the average citizen seems to live in a dream like illusion.” Yes. They deliberately propagandised the entire population, but overlooked the outcome of that. After a generation or so, those who are propagandised become the opinion makers and decision makers. It’s one thing to live in a bubble, it’s quite… Read more »